Most Commented
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professio...




Description material

Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional)
Language: English | Size:1.54 GB
Genre:eLearning
Files Included :
1 Course Overview.mp4 (5.14 MB)
MP4
1 Governance.mp4 (21.16 MB)
MP4
2 Confidentiality.mp4 (7.41 MB)
MP4
3 Integrity.mp4 (7.7 MB)
MP4
4 Availability.mp4 (7.43 MB)
MP4
5 Access Control Requirements.mp4 (22.29 MB)
MP4
6 Authorization.mp4 (2.76 MB)
MP4
7 Accountability.mp4 (11.86 MB)
MP4
1 Integrating Security into Software.mp4 (5.58 MB)
MP4
2 Complete Mediation.mp4 (4.6 MB)
MP4
3 Describe Psychological Acceptability.mp4 (4.1 MB)
MP4
4 Defence in Depth.mp4 (6.4 MB)
MP4
5 Least Privilege.mp4 (5.56 MB)
MP4
6 Economy of Mechanism.mp4 (11.42 MB)
MP4
7 Describe Resilience.mp4 (4.19 MB)
MP4
1 Domain Summary.mp4 (6.52 MB)
MP4
1 Course Overview.mp4 (5.31 MB)
MP4
1 Discovering Secure Software Requirements.mp4 (13.41 MB)
MP4
2 Gathering (Security) Requirements.mp4 (15 MB)
MP4
3 Identify Compliance Requirements.mp4 (10.05 MB)
MP4
1 Data Protection.mp4 (15.56 MB)
MP4
2 Data Lifecycle.mp4 (16.32 MB)
MP4
3 Implementing Data Protection.mp4 (16.6 MB)
MP4
4 Data Sharing.mp4 (12.6 MB)
MP4
1 Documenting Software Requirements.mp4 (13.31 MB)
MP4
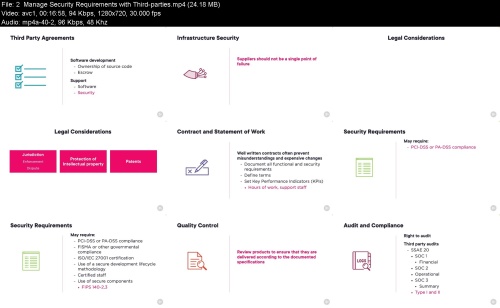
2 Manage Security Requirements with Third-parties.mp4 (24.18 MB)
MP4
1 Domain Summary.mp4 (6.97 MB)
MP4
01 Design Software Security Architecture.mp4 (7.37 MB)
MP4
02 Adequate Security.mp4 (6.06 MB)
MP4
03 Architecture Based Controls.mp4 (10.06 MB)
MP4
04 Client Server.mp4 (13.07 MB)
MP4
05 Web-based Architecture Risk.mp4 (6.89 MB)
MP4
06 Pervasive Computing.mp4 (10.28 MB)
MP4
07 Feature-based Risk.mp4 (15.38 MB)
MP4
08 Side Channel Vulnerabilities Speculative Execution.mp4 (10.4 MB)
MP4
09 Security Design Architecture - The Cloud.mp4 (9.21 MB)
MP4
10 Reasons to Migrate to the Cloud.mp4 (10.74 MB)
MP4
11 Security Design Architecture - Mobile Applications.mp4 (12.96 MB)
MP4
1 Course Overview.mp4 (2.65 MB)
MP4
1 Categorize Threats to Software Applications.mp4 (13.54 MB)
MP4
2 External Software Attack - Human.mp4 (13.71 MB)
MP4
3 Compromise of Operations.mp4 (7.39 MB)
MP4
4 Document Security Properties and Constraints.mp4 (13.8 MB)
MP4
5 Security Properties.mp4 (8.93 MB)
MP4
6 Performance.mp4 (8.08 MB)
MP4
7 Examine Architectural Risk Assessment.mp4 (10.27 MB)
MP4
1 Design Secure System Interfaces.mp4 (8 MB)
MP4
2 Upstream and Downstream Dependencies.mp4 (9.84 MB)
MP4
3 Interfaces.mp4 (5.67 MB)
MP4
4 Protocol Design Choices.mp4 (9.07 MB)
MP4
1 Design and Evaluate Software Security Architecture.mp4 (12.81 MB)
MP4
2 Operating System Security.mp4 (15.12 MB)
MP4
3 Credential Management.mp4 (6.3 MB)
MP4
4 Data Protection.mp4 (9.24 MB)
MP4
5 Database Security.mp4 (12.18 MB)
MP4
6 Programming Language Environments.mp4 (7.78 MB)
MP4
7 Secure Backup and Restoration Planning.mp4 (10.96 MB)
MP4
8 Design Security Review.mp4 (7.44 MB)
MP4
9 Perform Architectural Risk Assessment.mp4 (10.22 MB)
MP4
01 Secure Coding Practices.mp4 (10.41 MB)
MP4
02 Programming Considerations.mp4 (17.86 MB)
MP4
03 Input Validation.mp4 (10.58 MB)
MP4
04 Error Handling and Logging.mp4 (16.35 MB)
MP4
05 Protection of Output.mp4 (8.97 MB)
MP4
06 Session Management, Injection, and XSS.mp4 (12.85 MB)
MP4
07 Configuration Management.mp4 (9.04 MB)
MP4
08 Network and Storage Requirements.mp4 (9.04 MB)
MP4
09 Resource and Memory Management.mp4 (14.52 MB)
MP4
10 Sensitive Data Exposure and Access Control.mp4 (14.3 MB)
MP4
1 Course Overview (1).mp4 (2.02 MB)
MP4
1 Course Overview.mp4 (5 MB)
MP4
1 Secure Coding Practices.mp4 (8.25 MB)
MP4
2 Input Validation.mp4 (5.6 MB)
MP4
3 Error Handling and Logging.mp4 (14.92 MB)
MP4
4 Sensitive Data Exposure and Access Control.mp4 (18.81 MB)
MP4
5 Resource Management.mp4 (13.25 MB)
MP4
6 Configuration Management.mp4 (11.85 MB)
MP4
7 Programming Considerations.mp4 (9.49 MB)
MP4
8 Protection of Output.mp4 (9.18 MB)
MP4
1 Analyze Code for Security Risks.mp4 (7.78 MB)
MP4
2 Code Review.mp4 (6.63 MB)
MP4
3 Seeking out Vulnerabilities.mp4 (8.79 MB)
MP4
1 Software Code Risks.mp4 (8.15 MB)
MP4
2 Protected Code.mp4 (18.51 MB)
MP4
1 Implement Software Security Controls.mp4 (7.5 MB)
MP4
2 Protected Code.mp4 (15.1 MB)
MP4
1 Secure Code Analysis.mp4 (11.35 MB)
MP4
2 Code Review Methods.mp4 (8.43 MB)
MP4
3 Seeking Out Vulnerabilities.mp4 (7.94 MB)
MP4
1 Domain Summary.mp4 (5.61 MB)
MP4
1 Course Overview.mp4 (2.65 MB)
MP4
1 Develop Security Test Cases.mp4 (16.43 MB)
MP4
2 Testing the Box.mp4 (13.84 MB)
MP4
3 Vulnerability Assessments and Penetration Testing.mp4 (20.41 MB)
MP4
4 Scanning.mp4 (10.68 MB)
MP4
5 Ongoing Testing.mp4 (10.03 MB)
MP4
6 Environment Testing.mp4 (10.14 MB)
MP4
1 Develop Security Testing Strategy and Plan.mp4 (17.58 MB)
MP4
2 Develop or Obtain Security Test Data.mp4 (7.63 MB)
MP4
3 Testing Methodologies.mp4 (12.33 MB)
MP4
4 Database Integrity.mp4 (12.76 MB)
MP4
1 Documentation, Verification, and Validation.mp4 (9.2 MB)
MP4
2 Resolving Errors Found During Testing.mp4 (10.27 MB)
MP4
3 Documentation.mp4 (13.61 MB)
MP4
1 Course Overview.mp4 (4.92 MB)
MP4
1 Software Development Methodologies.mp4 (10.16 MB)
MP4
2 Incorporate Security into the SDLC.mp4 (23.1 MB)
MP4
1 Managing Software Lifecycle Risk.mp4 (18.22 MB)
MP4
2 Legal and Regulatory Issues.mp4 (12.23 MB)
MP4
3 Software Security Standards.mp4 (11.55 MB)
MP4
1 Managing Software Operational Security.mp4 (17.35 MB)
MP4
2 Version Control.mp4 (5.32 MB)
MP4
3 Security Metrics.mp4 (20.71 MB)
MP4
1 Decommissioning Software Securely.mp4 (11.27 MB)
MP4
2 Data Destruction.mp4 (13.61 MB)
MP4
1 Domain Summary.mp4 (7.49 MB)
MP4
1 Course Overview.mp4 (2.63 MB)
MP4
1 Evaluate Operational Risk.mp4 (14.36 MB)
MP4
2 Deployment Environment Hardening.mp4 (9.96 MB)
MP4
3 Assess Personnel Training and Integration.mp4 (4.91 MB)
MP4
1 Specify Secure Software Configuration.mp4 (16.05 MB)
MP4
2 Scheduling.mp4 (10.04 MB)
MP4
3 Securely Store and Manage Security Data.mp4 (12.16 MB)
MP4
4 Access Control.mp4 (9.72 MB)
MP4
5 Credentials.mp4 (11.56 MB)
MP4
6 Encryption Keys.mp4 (9.5 MB)
MP4
7 Post-implementation Security Testing.mp4 (4.31 MB)
MP4
1 Post-deployment and Resilience.mp4 (12.68 MB)
MP4
2 Post-implementation Support.mp4 (11.78 MB)
MP4
3 Continuous Monitoring.mp4 (15.03 MB)
MP4
4 Support Incident Response.mp4 (19.85 MB)
MP4
5 Support Continuity of Operations.mp4 (10.57 MB)
MP4
6 Delayed Recovery.mp4 (9.76 MB)
MP4
7 Disaster Recovery Planning.mp4 (13.73 MB)
MP4
8 Support Patch and Vulnerability Management.mp4 (12.27 MB)
MP4
1 Course Overview.mp4 (2.53 MB)
MP4
1 Evaluate Software Supply Chain Risk Management.mp4 (9.64 MB)
MP4
2 Document the Supply Chain.mp4 (10.32 MB)
MP4
3 Assess Supply Chain Risk.mp4 (6.94 MB)
MP4
4 Third-party Contracts.mp4 (11.3 MB)
MP4
5 Outsourcing Software Development.mp4 (9.99 MB)
MP4
1 Ascertain Code Repository Security.mp4 (10.32 MB)
MP4
2 Software Deployment.mp4 (10.35 MB)
MP4
3 Secure Build.mp4 (12.15 MB)
MP4
1 Assess Supply Chain Monitoring.mp4 (18.55 MB)
MP4
2 Supply Chain Risk Response.mp4 (10.97 MB)
MP4

Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).z01
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).z02
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).z03
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).zip

Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).z01
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).z02
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).z03
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).zip
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).z01
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).z02
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).z03
Pluralsight - Learning Path - CSSLP (Certified Secure Software Lifecycle Professional).zip
Join to our telegram Group
Information
Users of Guests are not allowed to comment this publication.
Users of Guests are not allowed to comment this publication.
Choose Site Language
Recommended news
Commented



![eM Client Pro 9.2.1735 Multilingual [Updated]](https://pikky.net/medium/wXgc.png)






![Movavi Video Editor 24.0.2.0 Multilingual [ Updated]](https://pikky.net/medium/qhrc.png)

