Most Commented
Learn Kali Linux From Scratch




Description material

Learn Kali Linux From Scratch
Published 2/2024
MP4 | Video: h264, 1920x1080 | Audio: AAC, 44.1 KHz
Language: English | Size: 2.88 GB | Duration: 4h 15m
Dive into ethical hacking with Kali Linux –- a beginner's guide to mastering the OS and essential cybersecurity skills.
What you'll learn
Master basic to advanced operations in Kali Linux
Navigate through hands-on exercises on virtual machines
Install Kali Linux seamlessly on any OS: Windows, Mac, Linux
Progress from beginner to advanced In using Linux Terminal
Discover Kali Linux apps and tools for diverse tasks
Learn System Administration and Account Access Control
Explore penetration testing tools and techniques
Learn how to use kali linux tools to crack passwords
Learn about different types of shells
and much more!
Requirements
A Computer with Network Connection
Any operating system will work (Windows, Linux, MacOS)
Very basic understanding of networking
Description
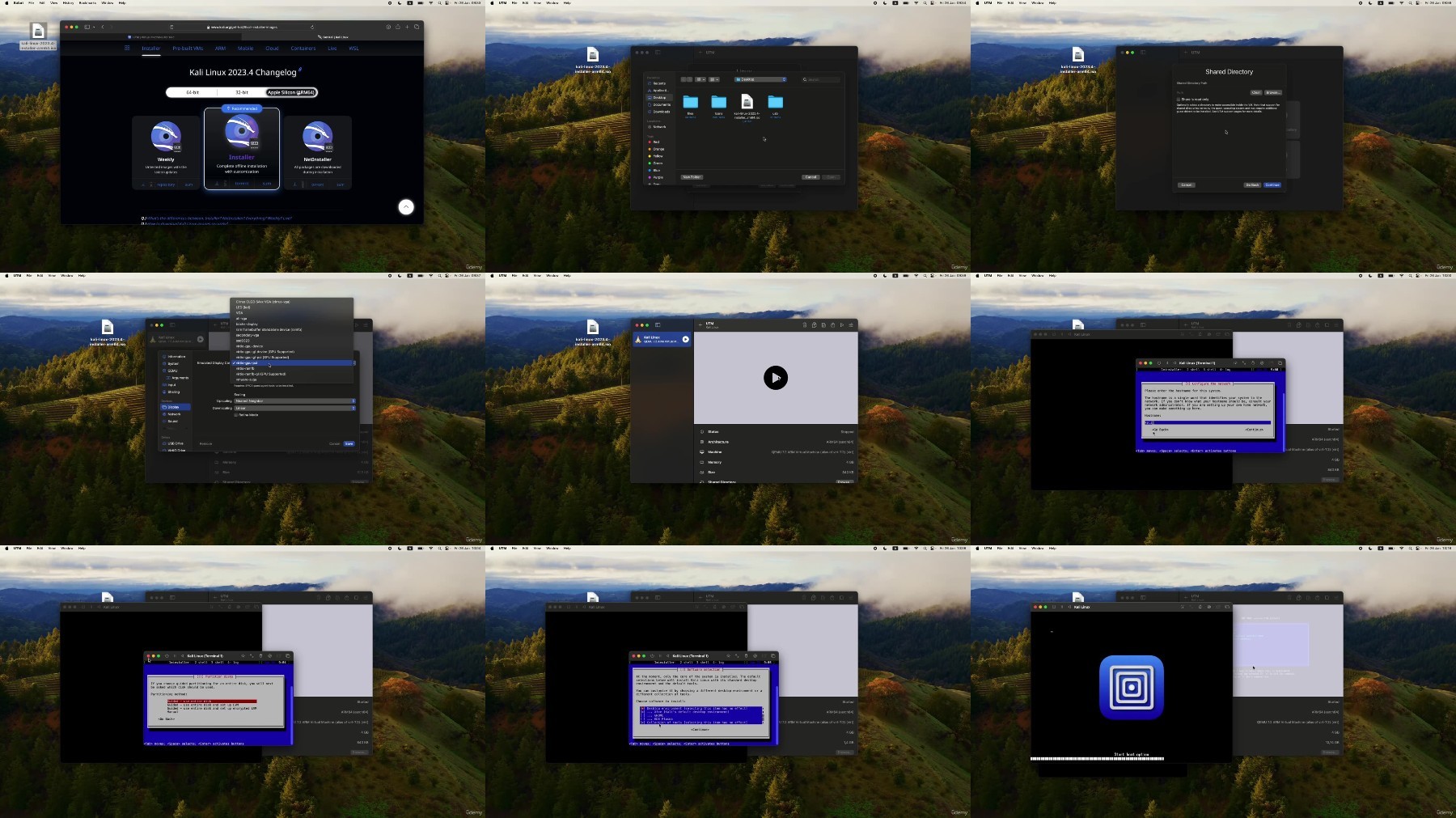
Join us on an exciting journey into the world of ethical hacking with our "Kali Linux For Beginners" course! Designed for beginners, this comprehensive guide covers everything from the basics of virtual machines and Kali Linux installation on various different operating systems to mastering terminal usage and exploring a variety of Kali Linux apps and tools. Grow your potential as you delve into the fascinating realm of penetration testing, learning both offensive and defensive strategies. Whether you're intrigued by Linux Operating Systems or eager to understand how hackers operate and which tools they use, this course equips you with practical skills and insights. Join us on this thrilling adventure and discover the power of Kali Linux – it's not just a course; it's a gateway to unlocking endless possibilities in the dynamic field of cybersecurity!Here is a list of topics that we cover:1) Introduction To The Course: - Welcome To The Course! - What is Kali Linux ?2) Setting Up Our Kali Linux: - Introduction To Virtual Machines - Virtual Box Download & Install - Downloading Kali Linux - Importing Kali Linux To Virtual Box - Kali Linux Installation In Virtual Box - Kali Linux Install On Mac Silicon - User Interface Introduction - Guest Additions & Network Settings - Keeping Kali Up To Date & Access Control Theory - Summary3) Performing Simple Tasks In Kali Linux: - Essential Terminal Commands - File Permissions In Practice - System Administration - Switching To Gnome GUI (Optional) - Learning With AI - Summary4) Shells: - Introduction To Shells - Reverse Shells In Practice - Telnet vs SSH - Exploring Z Shell - Summary5) Essential Tools In Kali: - Vim - Nano - Wget - Curl - John The Ripper - Hashcat - Summary6) Penetration Testing With Kali - Penetration Testing Process - Google Dorking - Downloading & Importing OWASP VM - Nmap - DNS Lookups (Reconnaissance) - Burp Suite (Gaining Access) - Enumerating Hidden Web Pages (Scanning) - Hosting A Fake Website
Overview
Section 1: Introduction To The Course
Lecture 1 Welcome To The Course!
Lecture 2 What Is Kali Linux ?
Section 2: Setting Up Our Kali Linux
Lecture 3 Introduction To Virtual Machines
Lecture 4 Virtual Box Download & Install
Lecture 5 Downloading Kali Linux
Lecture 6 Importing Kali Linux To Virtual Box
Lecture 7 Kali Linux Installation In Virtual Box
Lecture 8 (For M1/M2/M3 chip MAC Users) - Kali Linux Install
Lecture 9 User Interface Introduction
Lecture 10 Note: Guest Additions
Lecture 11 Guest Additions & Network Settings
Lecture 12 Keeping Kali Up-To-Date & Access Control Theory
Lecture 13 Summary
Section 3: Performing Simple Tasks In Kali Linux
Lecture 14 Essential Terminal Commands
Lecture 15 File Permissions In Practice
Lecture 16 System Administration
Lecture 17 Switching To Gnome GUI (Optional)
Lecture 18 Learning With AI
Lecture 19 Summary
Section 4: Shells
Lecture 20 Introduction To Shells
Lecture 21 Reverse Shells In Practice
Lecture 22 Telnet vs SSH
Lecture 23 Exploring Z Shell
Lecture 24 Summary
Section 5: Essential Tools In Kali
Lecture 25 Vim
Lecture 26 Nano
Lecture 27 Wget
Lecture 28 Curl
Lecture 29 John The Ripper
Lecture 30 Hashcat
Lecture 31 Summary
Section 6: Penetration Testing With Kali
Lecture 32 Penetration Testing Process
Lecture 33 Google Dorking (Reconnaissance)
Lecture 34 Downloading & Importing OWASP VM
Lecture 35 Nmap (Scanning)
Lecture 36 DNS Lookups (Reconnaissance)
Lecture 37 Burp Suite (Gaining Access)
Lecture 38 Enumerating Hidden Web Pages (Scanning)
Lecture 39 Hosting A Fake Website
If you are starting from scratch with Linux and aim to navigate Kali Linux, this course is tailored for your learning journey,For those with a foundational grasp of ethical hacking, this course offers a pathway to using those skills specifically with Kali Linux,Anybody Interested In learning Basic System Administration On Linux Systems
https://rapidgator.net/file/736a781746f8892be5a1a2a7aaaec62a/Udemy_Learn_Kali_Linux_From_Scratch_2024-5.part1.rar
https://rapidgator.net/file/97f617cdd3a838d659cc26c9af2b2675/Udemy_Learn_Kali_Linux_From_Scratch_2024-5.part2.rar

https://filestore.me/zqca9s0mhtu6/Udemy_Learn_Kali_Linux_From_Scratch_2024-5.part1.rar
https://filestore.me/hmi04sjo8jjh/Udemy_Learn_Kali_Linux_From_Scratch_2024-5.part2.rar
What you'll learn
Master basic to advanced operations in Kali Linux
Navigate through hands-on exercises on virtual machines
Install Kali Linux seamlessly on any OS: Windows, Mac, Linux
Progress from beginner to advanced In using Linux Terminal
Discover Kali Linux apps and tools for diverse tasks
Learn System Administration and Account Access Control
Explore penetration testing tools and techniques
Learn how to use kali linux tools to crack passwords
Learn about different types of shells
and much more!
Requirements
A Computer with Network Connection
Any operating system will work (Windows, Linux, MacOS)
Very basic understanding of networking
Description
Join us on an exciting journey into the world of ethical hacking with our "Kali Linux For Beginners" course! Designed for beginners, this comprehensive guide covers everything from the basics of virtual machines and Kali Linux installation on various different operating systems to mastering terminal usage and exploring a variety of Kali Linux apps and tools. Grow your potential as you delve into the fascinating realm of penetration testing, learning both offensive and defensive strategies. Whether you're intrigued by Linux Operating Systems or eager to understand how hackers operate and which tools they use, this course equips you with practical skills and insights. Join us on this thrilling adventure and discover the power of Kali Linux – it's not just a course; it's a gateway to unlocking endless possibilities in the dynamic field of cybersecurity!Here is a list of topics that we cover:1) Introduction To The Course: - Welcome To The Course! - What is Kali Linux ?2) Setting Up Our Kali Linux: - Introduction To Virtual Machines - Virtual Box Download & Install - Downloading Kali Linux - Importing Kali Linux To Virtual Box - Kali Linux Installation In Virtual Box - Kali Linux Install On Mac Silicon - User Interface Introduction - Guest Additions & Network Settings - Keeping Kali Up To Date & Access Control Theory - Summary3) Performing Simple Tasks In Kali Linux: - Essential Terminal Commands - File Permissions In Practice - System Administration - Switching To Gnome GUI (Optional) - Learning With AI - Summary4) Shells: - Introduction To Shells - Reverse Shells In Practice - Telnet vs SSH - Exploring Z Shell - Summary5) Essential Tools In Kali: - Vim - Nano - Wget - Curl - John The Ripper - Hashcat - Summary6) Penetration Testing With Kali - Penetration Testing Process - Google Dorking - Downloading & Importing OWASP VM - Nmap - DNS Lookups (Reconnaissance) - Burp Suite (Gaining Access) - Enumerating Hidden Web Pages (Scanning) - Hosting A Fake Website
Overview
Section 1: Introduction To The Course
Lecture 1 Welcome To The Course!
Lecture 2 What Is Kali Linux ?
Section 2: Setting Up Our Kali Linux
Lecture 3 Introduction To Virtual Machines
Lecture 4 Virtual Box Download & Install
Lecture 5 Downloading Kali Linux
Lecture 6 Importing Kali Linux To Virtual Box
Lecture 7 Kali Linux Installation In Virtual Box
Lecture 8 (For M1/M2/M3 chip MAC Users) - Kali Linux Install
Lecture 9 User Interface Introduction
Lecture 10 Note: Guest Additions
Lecture 11 Guest Additions & Network Settings
Lecture 12 Keeping Kali Up-To-Date & Access Control Theory
Lecture 13 Summary
Section 3: Performing Simple Tasks In Kali Linux
Lecture 14 Essential Terminal Commands
Lecture 15 File Permissions In Practice
Lecture 16 System Administration
Lecture 17 Switching To Gnome GUI (Optional)
Lecture 18 Learning With AI
Lecture 19 Summary
Section 4: Shells
Lecture 20 Introduction To Shells
Lecture 21 Reverse Shells In Practice
Lecture 22 Telnet vs SSH
Lecture 23 Exploring Z Shell
Lecture 24 Summary
Section 5: Essential Tools In Kali
Lecture 25 Vim
Lecture 26 Nano
Lecture 27 Wget
Lecture 28 Curl
Lecture 29 John The Ripper
Lecture 30 Hashcat
Lecture 31 Summary
Section 6: Penetration Testing With Kali
Lecture 32 Penetration Testing Process
Lecture 33 Google Dorking (Reconnaissance)
Lecture 34 Downloading & Importing OWASP VM
Lecture 35 Nmap (Scanning)
Lecture 36 DNS Lookups (Reconnaissance)
Lecture 37 Burp Suite (Gaining Access)
Lecture 38 Enumerating Hidden Web Pages (Scanning)
Lecture 39 Hosting A Fake Website
If you are starting from scratch with Linux and aim to navigate Kali Linux, this course is tailored for your learning journey,For those with a foundational grasp of ethical hacking, this course offers a pathway to using those skills specifically with Kali Linux,Anybody Interested In learning Basic System Administration On Linux Systems

https://rapidgator.net/file/736a781746f8892be5a1a2a7aaaec62a/Udemy_Learn_Kali_Linux_From_Scratch_2024-5.part1.rar
https://rapidgator.net/file/97f617cdd3a838d659cc26c9af2b2675/Udemy_Learn_Kali_Linux_From_Scratch_2024-5.part2.rar

https://filestore.me/zqca9s0mhtu6/Udemy_Learn_Kali_Linux_From_Scratch_2024-5.part1.rar
https://filestore.me/hmi04sjo8jjh/Udemy_Learn_Kali_Linux_From_Scratch_2024-5.part2.rar
Join to our telegram Group
Information
Users of Guests are not allowed to comment this publication.
Users of Guests are not allowed to comment this publication.
Choose Site Language
Recommended news
Commented


![eM Client Pro 9.2.1735 Multilingual [Updated]](https://pikky.net/medium/wXgc.png)





![Movavi Video Editor 24.0.2.0 Multilingual [ Updated]](https://pikky.net/medium/qhrc.png)

