Most Commented
Pluralsight CISSP Certified Information Systems Security Professional Exam




Description material

12.12 GB | 00:10:59 | mp4 | 1920X1080 | 16:9
Genre:eLearning |Language:English
Files Included :
001 Course Overview (34.8 MB)
001 Introduction (98.99 MB)
002 Security Concepts Governance and Ethics (38.46 MB)
003 Information Security Concepts (23.33 MB)
004 The Integrity Pillar (30.21 MB)
005 Providing Availability (24.02 MB)
006 Non-repudiation (29.11 MB)
007 Security Governance (44.76 MB)
008 Organizational Roles and Responsibilities (81.24 MB)
009 Security Control Frameworks (42.32 MB)
010 Due Care and Due Diligence (17.05 MB)
011 Ethics (40.7 MB)
012 ISC2 Code of Ethics (24.24 MB)
001 Policies and Frameworks (32.65 MB)
002 Standards Procedures and Baselines (25.74 MB)
003 Personnel Security Policies and Procedures (24.31 MB)
004 Employment (31.95 MB)
005 Personnel Safety and Security (80.49 MB)
006 Security Awareness Education and Training (36.84 MB)
007 Awareness Program Deployment (52.03 MB)
008 Training and Education (26.81 MB)
001 Legal and Regulatory Issues (17.8 MB)
002 Privacy Laws and Regulations (45.53 MB)
003 Cybercrime and Data Breaches (27.37 MB)
004 Protection of IP (28.9 MB)
001 Domain Summary (28.41 MB)
001 Course Overview (34.4 MB)
001 Principles of Risk Management (118.35 MB)
002 Overview of Risk Management (28.88 MB)
003 Types of Risk and Context (49.15 MB)
001 Threat Modeling and Risk Assessment (27.62 MB)
002 Threat Modeling (45.71 MB)
003 The Attack Surface (20.77 MB)
004 Analysis of Risk (60.25 MB)
001 Risk Response and Controls (58.26 MB)
002 Control Selection (47.88 MB)
001 Risk Monitoring and Reporting (20.28 MB)
002 Risk Reporting (20.18 MB)
003 Supply Chain Risk Management (36.51 MB)
004 Third-party Hardware Risk (30.32 MB)
005 Supply Chain Risk Assessment Methodology (38.16 MB)
001 Domain Summary (27.15 MB)
001 Course Overview (35.51 MB)
001 Asset Security (98.05 MB)
002 Asset Classification (35.11 MB)
003 Asset Management Principles (44.85 MB)
004 Asset Ownership and Valuation (28.79 MB)
005 Asset Classification (55.42 MB)
006 Asset Valuation (23.9 MB)
007 Asset Management Lifecycle (35.73 MB)
008 Asset Protection (24.08 MB)
009 Asset Management Procedures (15.05 MB)
010 Asset Retention (53.99 MB)
001 The Data Lifecycle (58.67 MB)
002 Data Lifecycle - CreationCollection (34.12 MB)
003 Data ClassificationCategorization Criteria (339.77 MB)
004 Data Protection (141.08 MB)
005 Data Lifecycle - Store (393.91 MB)
006 Roles in Data Protection (21.39 MB)
007 Data Use (73.17 MB)
008 Data Retention (54.96 MB)
001 Domain Summary (31.93 MB)
001 Course Overview (40.52 MB)
001 Secure Design (106.85 MB)
002 Secure Design Principles (17.97 MB)
003 Integrating Security into Systems Lifecycles (26.84 MB)
004 Architectural Models (65.42 MB)
005 Gathering Security Requirements (82.59 MB)
006 Security Baselines (29.46 MB)
007 Tailoring (37.9 MB)
001 Implementation and Maintenance (63.71 MB)
002 Evaluation Criteria (64.25 MB)
003 Deployment and Operations (36.94 MB)
004 End-of-life (24.85 MB)
001 Domain Summary (19.55 MB)
001 Course Overview (40.52 MB)
001 Secure Design (106.85 MB)
002 Secure Design Principles (17.97 MB)
003 Integrating Security into Systems Lifecycles (26.84 MB)
004 Architectural Models (65.42 MB)
005 Gathering Security Requirements (82.59 MB)
006 Control Selection (41.63 MB)
007 Security Baselines (29.46 MB)
008 Tailoring (37.9 MB)
001 Implementation and Maintenance (63.71 MB)
002 Evaluation Criteria (64.25 MB)
003 Deployment and Operations (36.94 MB)
004 End-of-life (24.85 MB)
001 Domain Summary (19.55 MB)
001 Course Overview (39.19 MB)
001 Security Controls and Vulnerabilities (78.02 MB)
002 Secure Design Principles (61.2 MB)
003 Secure Access Models (35.49 MB)
004 Security Models (41.95 MB)
005 Biba Integrity Model (26.81 MB)
006 Other Security Models (33.37 MB)
001 Secure Systems and Components (70.82 MB)
002 Traditional IT Systems Architecture (39.41 MB)
003 Centralized and Decentralized Architecture (55.96 MB)
004 Non-traditional IT Architectures (67.26 MB)
005 High-performance Systems (36.97 MB)
006 Cloud Architecture (30.85 MB)
007 Cloud Security Responsibilities (58.23 MB)
001 Domain Summary (20.39 MB)
001 Course Overview (45.68 MB)
001 Physical Security Controls and Design (78.53 MB)
002 Facility and Physical Security (34.01 MB)
003 Design Perimeter Controls (63.56 MB)
004 Internal Physical Security Threats (19.33 MB)
005 Shared Facility (82.04 MB)
006 Walls and Doors (28.71 MB)
001 Environmental Controls (32.18 MB)
002 Power (17.63 MB)
001 Domain Summary (23.72 MB)
001 Course Overview (38.62 MB)
001 Concepts of Cryptography (35.36 MB)
002 Symmetric Cryptography (40.65 MB)
003 Asymmetric Algorithms (44.01 MB)
004 Message Integrity (33.05 MB)
005 Using Cryptography Securely (49.47 MB)
006 Key Management (54.45 MB)
007 Quantum (29.66 MB)
008 Designing Encryption (68.43 MB)
001 Cryptanalysis (48.52 MB)
002 Other Attacks (129.43 MB)
001 Domain Summary (25.02 MB)
001 Course Overview (35.57 MB)
001 Communication and Network Security for the CISSP (72.54 MB)
002 Network Protocols (34.65 MB)
003 Continuing Down the Stack - Presentation (24.71 MB)
004 Continuing Down the Stack - Transport (33.51 MB)
005 Continuing Down the Stack - Network (38.64 MB)
006 Continuing Down the Stack - Data Link (29.45 MB)
007 OSI and TCPIP (74.29 MB)
008 Multi-layer Protocols (114.55 MB)
001 Secure Network Design (48.98 MB)
002 Hardware vs Software (73.77 MB)
003 Network Architecture and Management (58.83 MB)
004 Wide Area Networks (36.89 MB)
005 Wireless and Cellular Networks (35.43 MB)
006 G (105.81 MB)
007 Example of an Attack (54 MB)
008 Botnets (30.01 MB)
001 Network Components and Monitoring (31.5 MB)
002 Network Access (19.13 MB)
003 Protection of Networks (33.91 MB)
004 Network Operations Management (83.85 MB)
005 Intrusion (59.57 MB)
006 Anti-malware (33.69 MB)
001 Domain Summary (21.38 MB)
001 Course Overview (33.59 MB)
001 Introduction (71.05 MB)
002 Identity-based Access Controls (98.22 MB)
003 Authentication (104.79 MB)
004 Physical and Logical Access Controls (49.31 MB)
005 Access to Desktops (42.86 MB)
001 Implementing Access Controls (17.45 MB)
002 Access Control Theory and Implementations (39.89 MB)
003 Implementing Access Controls (51.82 MB)
004 Single Sign-on (55.45 MB)
005 Access Control Management (15.22 MB)
001 Managing the Identity Management Lifecycle (29.75 MB)
002 Provisioning (34.41 MB)
003 De-provisioning (9.55 MB)
001 Domain Summary (26.07 MB)
001 Course Overview (38.99 MB)
001 Introduction (100.02 MB)
002 Security Testing Strategy (44.01 MB)
003 Enabling Assessment (50.31 MB)
004 Planning the Assessment (31.87 MB)
005 The Test Strategy (54.68 MB)
006 Conduct Security Controls Testing (26.72 MB)
007 Vulnerability Assessments (25.28 MB)
008 Penetration Testing (57.96 MB)
009 Conducting a Penetration Test (29.9 MB)
001 Tests and Remediation (42.24 MB)
002 Assessment Criteria (21.45 MB)
003 Conduct or Facilitate Security Audits (56.23 MB)
004 Conducting an Audit (7.82 MB)
005 Format of an Audit Report (19.51 MB)
001 Domain Summary (30.88 MB)
001 Course Overview (44.13 MB)
001 Introduction (80.93 MB)
002 Operations Management (55.38 MB)
003 Log Management (68.03 MB)
004 UEBA (43.23 MB)
005 Security and Data Protection (69.07 MB)
006 Continuous Monitoring (140.36 MB)
001 Managing Security (61.45 MB)
002 Configuration Management (46.85 MB)
003 Service Level Agreements (92.21 MB)
004 Security Operations Monitoring (27.96 MB)
005 Threat Intelligence (22.03 MB)
001 Domain Summary (35.85 MB)
001 Course Overview (37.79 MB)
001 Introduction (49.31 MB)
002 Software Development Methodologies (25.95 MB)
003 SDLC Methodologies (92.59 MB)
004 Evolution of Software Deployments (64.9 MB)
005 Software Project Management (80.45 MB)
006 Gathering (Security) Requirements (43.93 MB)
007 Software Project Planning (32.66 MB)
008 Project Requirements (46.5 MB)
009 Project Design (66.22 MB)
001 Secure Coding (39.27 MB)
002 Secure Coding Practices (54.24 MB)
003 Good Coding Practices (57.45 MB)
004 Code Management (63.62 MB)
005 Deployment (35.65 MB)
006 Operations (29.46 MB)
007 Databases (40.48 MB)
008 Database Security (13.2 MB)
009 Database Structure (48.85 MB)
010 Database Security Issues (38.06 MB)
001 Software Security Testing (87.45 MB)
002 Performance Testing (33.61 MB)
003 Production-based Testing (44.61 MB)
004 Ongoing Testing (45.34 MB)
005 Security of Third-party Software (30.57 MB)
001 Domain Summary (15.88 MB)
001 Course Overview (39.63 MB)
001 Security Operations Business Resilience and Incident Management (59.47 MB)
002 Business Resilience and Incident Management (25.77 MB)
003 Business Impact Analysis (104.26 MB)
004 Critical Business Functions (59.04 MB)
005 Incident Management Planning (58.61 MB)
006 Response Planning (15.29 MB)
007 Incident Management (87.95 MB)
008 Incident Response (30.33 MB)
009 Lessons Learned (51.02 MB)
001 Business Continuity and Disaster Recovery (61.51 MB)
002 Evidence Handling (52.06 MB)
003 Interviews (19.44 MB)
004 Documentation and Reporting (23.82 MB)
005 Selecting Recovery Strategies (30.91 MB)
006 Recovery Sites (84.11 MB)
007 Security in Disaster Recovery Plans (56.17 MB)
001 Implementing and Testing the BC and DR Plans (67.24 MB)
002 Maintaining Business Continuity Plans (27.16 MB)
001 Domain Summary (23.02 MB)
001 Course Overview (11.33 MB)
001 Exam Tips and Tricks for the CISSP (136.71 MB)
002 The CISSP Study Plan (149.41 MB)
003 Full Scope Studying (79.05 MB)
001 The CISSP Exam Day (63.63 MB)
002 Exam Tips (38.8 MB)
[center]
Screenshot
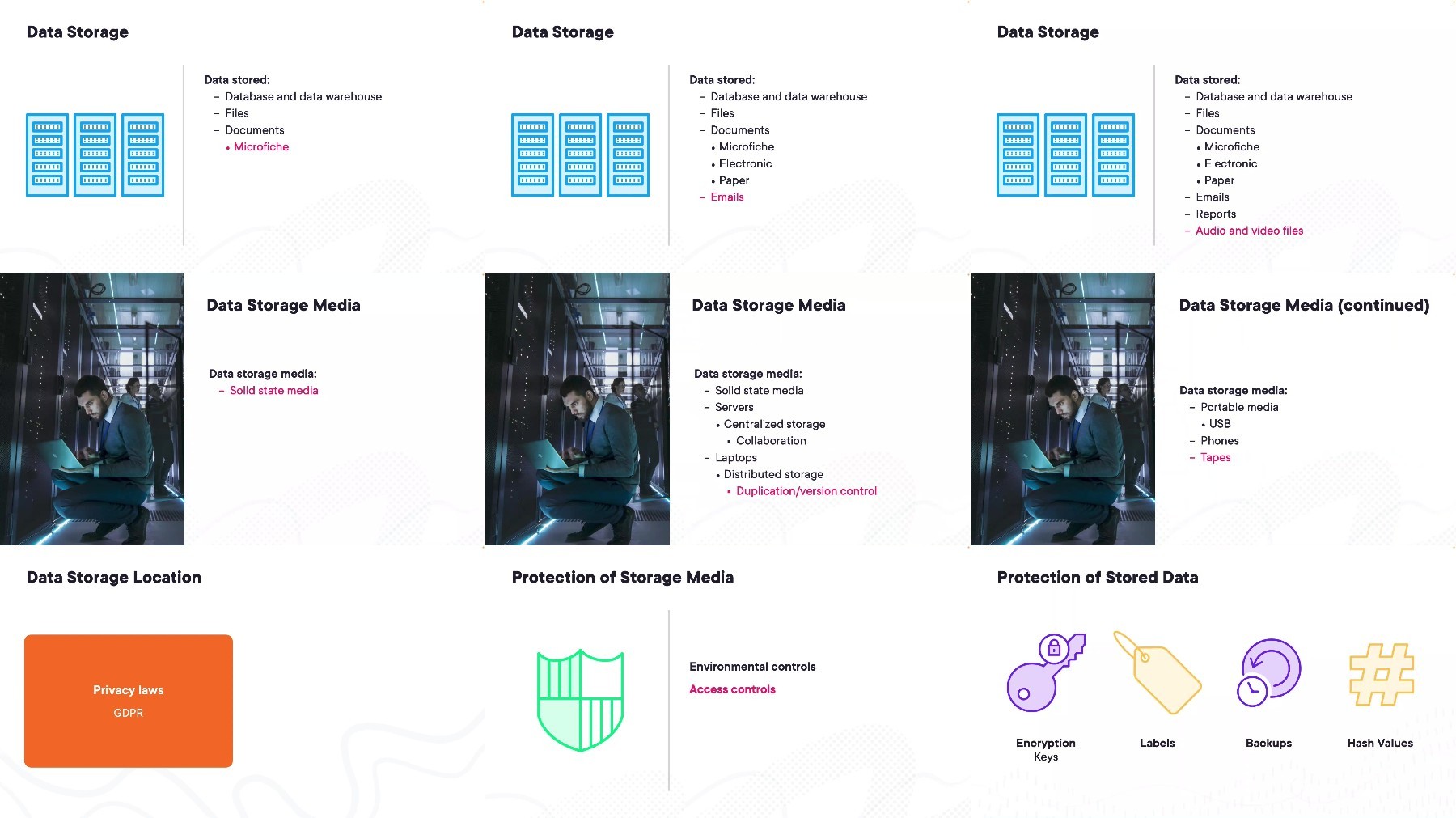
[/center]
RapidGator
Warning! You are not allowed to view this text.
TurboBit
Warning! You are not allowed to view this text.
FileAxa
Warning! You are not allowed to view this text.
Join to our telegram Group
Information
Users of Guests are not allowed to comment this publication.
Users of Guests are not allowed to comment this publication.
Choose Site Language
Recommended news
Commented



![eM Client Pro 9.2.1735 Multilingual [Updated]](https://pikky.net/medium/wXgc.png)






![Movavi Video Editor 24.0.2.0 Multilingual [ Updated]](https://pikky.net/medium/qhrc.png)

