Most Commented
Cybersecurity Prevention and Detection 2nd Edition (Video Collection)




Description material

3.28 GB | 00:23:06 | mp4 | 1280X720 | 16:9
Genre:eLearning |Language:English
Files Included :
001 Introduction (3.9 MB)
001 Learning objectives (2.9 MB)
002 1 1 Threat actors Part 1 (51.04 MB)
003 1 2 Threat actors Part 2 (16.78 MB)
004 1 3 Confidence levels (18.18 MB)
005 1 4 Threat hunting (17.37 MB)
001 Learning objectives (5.63 MB)
002 2 1 Network-related (73.56 MB)
003 2 2 Host-related (39.26 MB)
004 2 3 Application-related (12.74 MB)
005 2 4 Malicious Activity Indicators (22.47 MB)
001 Learning objectives (3.94 MB)
002 3 1 Tools Part 1 (39.36 MB)
003 3 2 Tools Part 2 (37.08 MB)
004 3 3 Common techniques Part 1 (54.28 MB)
005 3 4 Common techniques Part 2 (48.73 MB)
006 3 5 Common techniques Part 3 (60.75 MB)
007 3 6 Programming languagesscripting (23.92 MB)
001 Learning objectives (2.44 MB)
002 4 1 Cyber kill chains (21.51 MB)
003 4 2 Diamond Model of Intrusion Analysis (9.61 MB)
004 4 3 MITRE ATT&CK Part 1 (32.69 MB)
005 4 4 MITRE ATT&CK Part 2 (36.41 MB)
006 4 5 Open Source Security Testing Methodology Manual (OSS TMM) (5.07 MB)
007 4 6 OWASP Testing Guide (15.4 MB)
001 Learning objectives (3.7 MB)
002 5 1 Attack Frameworks Part 1 (35.26 MB)
003 5 2 Attack Frameworks Part 2 (22.07 MB)
004 5 3 Threat Research (15.24 MB)
006 5 5 Wireless Analysis Techniques (18.12 MB)
001 Learning objectives (2.07 MB)
002 6 1 Understanding Results (17.99 MB)
003 6 2 Web Application Scanners (4.07 MB)
004 6 3 Infrastructure Vulnerability Scanner (8.57 MB)
005 6 4 Software Assessment Tools and Techniques (2.69 MB)
006 6 5 Wireless Assessment (8.08 MB)
007 6 6 Cloud Infrastructure Assessment (3.65 MB)
001 Learning objectives (2.09 MB)
002 7 1 Mobile (10.89 MB)
005 7 4 APTs (24.94 MB)
007 7 6 SOC and FPGA (48.13 MB)
008 7 7 Physical Access Control (3.52 MB)
011 7 10 Defending Critical Infrastructure (37.18 MB)
014 7 13 Verifications and Quality Controls (25.27 MB)
001 Threat Intelligence and Threat Hunting Summary (1.14 MB)
001 Introduction (4.55 MB)
001 Learning objectives (1.69 MB)
002 1 1 Privacy vs Security (15.62 MB)
003 1 2 Non-technical Controls (13.81 MB)
004 1 3 Classification, Ownership, Retention, and Data Types (26.47 MB)
005 1 4 Confidentiality, Legal Requirements, and Data Sovereignty (21.11 MB)
006 1 5 Data Minimization, Purpose Limitation, and NDA (3.71 MB)
007 1 6 Technical Controls (2.79 MB)
008 1 7 Encryption (12.54 MB)
009 1 8 Data Loss Prevention (DLP) (1.9 MB)
010 1 9 Data Masking and Deidentification (7.22 MB)
011 1 10 Tokenization (3.11 MB)
012 1 11 Digital Rights Management (DRM) and Watermarking (7.7 MB)
013 1 12 Geographic Access Requirements (5.93 MB)
014 1 13 Access Controls (2.8 MB)
001 Learning objectives (1.87 MB)
002 2 1 Business Impact and Risk Calculation (2.95 MB)
003 2 2 Communication Risk Factors and Risk Prioritization (13.87 MB)
004 2 3 System Assessments (8.55 MB)
005 2 4 Compensating Controls and Training - Part 1 (26.11 MB)
006 2 5 Compensating Controls and Training - Part 2 (18.04 MB)
007 2 6 Supply Chain Assessment (8.63 MB)
001 Learning objectives (1.9 MB)
002 3 1 Frameworks (5.82 MB)
003 3 2 AUP, Password Policies, Data Ownership, and Other Procedures (21.47 MB)
004 3 3 Control Types (21.47 MB)
005 3 4 Audits and Assessments (10.83 MB)
001 Learning objectives (1.7 MB)
002 4 1 Event Logs (6.15 MB)
003 4 2 Syslogs (18.76 MB)
004 4 3 Firewall Logs (23.51 MB)
005 4 4 Web Application Firewall (WAF) (18.09 MB)
006 4 5 Proxy (34.94 MB)
007 4 6 Intrusion Detection and Prevention (IDSIPS) (21.76 MB)
008 4 7 Impact Analysis (48.63 MB)
009 4 8 Organizations Impact vs Localized Impact (3.59 MB)
010 4 9 Immediate vs Total (2.84 MB)
001 Learning objectives (1.72 MB)
002 5 1 Security Information and Event Management (SIEM) - Part 1 (16.61 MB)
003 5 2 Security Information and Event Management (SIEM) - Part 2 (30.7 MB)
004 5 3 Rule Writing (10.68 MB)
005 5 4 Known-bad Internet Protocol (IP) (8.64 MB)
001 Learning objectives (1.92 MB)
002 6 1 Malicious Payload (28.43 MB)
003 6 2 Domain Keys Identified Mail (DKIM) (19.43 MB)
004 6 3 Domain-based Message (15.33 MB)
005 6 4 Embedded Links (7.41 MB)
006 6 5 Impersonation (2.79 MB)
007 6 6 Header (7.17 MB)
001 Learning objectives (2.17 MB)
002 7 1 Workflow Orchestration (20.08 MB)
003 7 2 Security Orchestration (5.99 MB)
004 7 3 Security Orchestration, Automation, and Response (SOAR) (9.49 MB)
005 7 4 Scripting (4.69 MB)
006 7 5 Application Programming Interface (API) Integration (8.26 MB)
007 7 6 Automated Malware Signature Creation (3.92 MB)
008 7 7 Data Encrichment (7.3 MB)
009 7 8 Threat Feed Combination (4.99 MB)
010 7 9 Machine Learning (35.56 MB)
011 7 10 Security Content Automation Protocol (SCAP) (4.85 MB)
012 7 11 Continuous Integration (6.51 MB)
013 7 12 Continuous Deployment and Delivery (3.39 MB)
001 System and Privacy Data Protection Summary (3 MB)
001 Introduction (4.09 MB)
001 Learning objectives (1.36 MB)
002 1 1 Malware Threat Landscape (86.63 MB)
003 1 2 Malware Analysis (11.04 MB)
004 1 3 Malware Analysis Overview (13.26 MB)
001 Learning objectives (1.4 MB)
002 2 1 Why Set Up a Malware Lab (21.62 MB)
003 2 2 How to Correctly Set Up a Lab (33.78 MB)
001 Learning objectives (3.11 MB)
002 3 1 Cuckoo Sandbox (16.78 MB)
003 3 2 Other Sandbox Systems (2.2 MB)
004 3 3 Networking and Internet Connections (11.63 MB)
005 3 4 Sandbox and Network (24.66 MB)
001 Learning objectives (1.58 MB)
002 4 1 Wireshark (14.8 MB)
003 4 2 Column Setup (15.91 MB)
001 Learning objectives (2.37 MB)
002 5 1 PE File Format (7.01 MB)
003 5 2 Image Header (6.48 MB)
004 5 3 Entry Points (59.54 MB)
001 Learning objectives (2.18 MB)
002 6 1 Registry Persistence (13.91 MB)
003 6 2 Analyzing for Persistence (11.09 MB)
004 6 3 Other Techniques (15.42 MB)
001 Learning objectives (1.8 MB)
002 7 1 What to Look for (16.41 MB)
001 Malware and Incident Response LiveLessons Summary (3.41 MB)
001 Introduction (3.34 MB)
001 Learning objectives (3.99 MB)
002 1 1 Log ingestion Part 1 (101.11 MB)
003 1 2 Log ingestion Part 2 (112.42 MB)
004 1 3 Operating system (OS) concepts (49.65 MB)
005 1 4 Infrastructure concepts (85.15 MB)
006 1 5 Network architecture (47.78 MB)
007 1 6 Identity and access management (114.75 MB)
008 1 7 Encryption (72.49 MB)
009 1 8 Sensitive data protection (20.97 MB)
001 Learning objectives (2.56 MB)
002 2 1 Standardize processes (32.74 MB)
003 2 2 Streamline operations (18.3 MB)
004 2 3 Technology and tool integration (83.12 MB)
001 Learning objectives (4.23 MB)
002 3 1 Cross-site scripting (11.82 MB)
003 3 2 Overflow vulnerabilities (17.11 MB)
004 3 3 Data poisoning (16.09 MB)
005 3 4 Broken access control (16.39 MB)
006 3 5 Cryptographic failures (22.65 MB)
007 3 6 Injection flaws (16.69 MB)
008 3 7 Cross-site request forgery (17.28 MB)
009 3 8 Directory traversal (19.34 MB)
010 3 9 Insecure design (14.77 MB)
011 3 10 Security misconfiguration (6.34 MB)
012 3 11 End-of-life or outdated components (13.76 MB)
013 3 12 Identification and authentication failures (26.14 MB)
014 3 13 Server-side request forgery (11.64 MB)
015 3 14 Remote code execution (19.36 MB)
016 3 15 Privilege escalation (25.06 MB)
001 Learning objectives (2.54 MB)
002 4 1 Compensating controls (7.18 MB)
003 4 2 Control types (23.01 MB)
004 4 3 Patching and configuration management (14.8 MB)
005 4 4 Maintenance windows (19.69 MB)
006 4 5 Exceptions (14.64 MB)
007 4 6 Risk management principles (31.6 MB)
008 4 7 Policies, governance, and service-level objectives (SLOs) (8.93 MB)
009 4 8 Prioritization and escalation (10.63 MB)
010 4 9 Attack surface management (23.43 MB)
011 4 10 Secure coding best practices (37.39 MB)
012 4 11 Secure software development life cycle (SDLC) (31.74 MB)
013 4 12 Threat modeling (41.62 MB)
001 Secure Operations and Protections Summary (1.29 MB)]
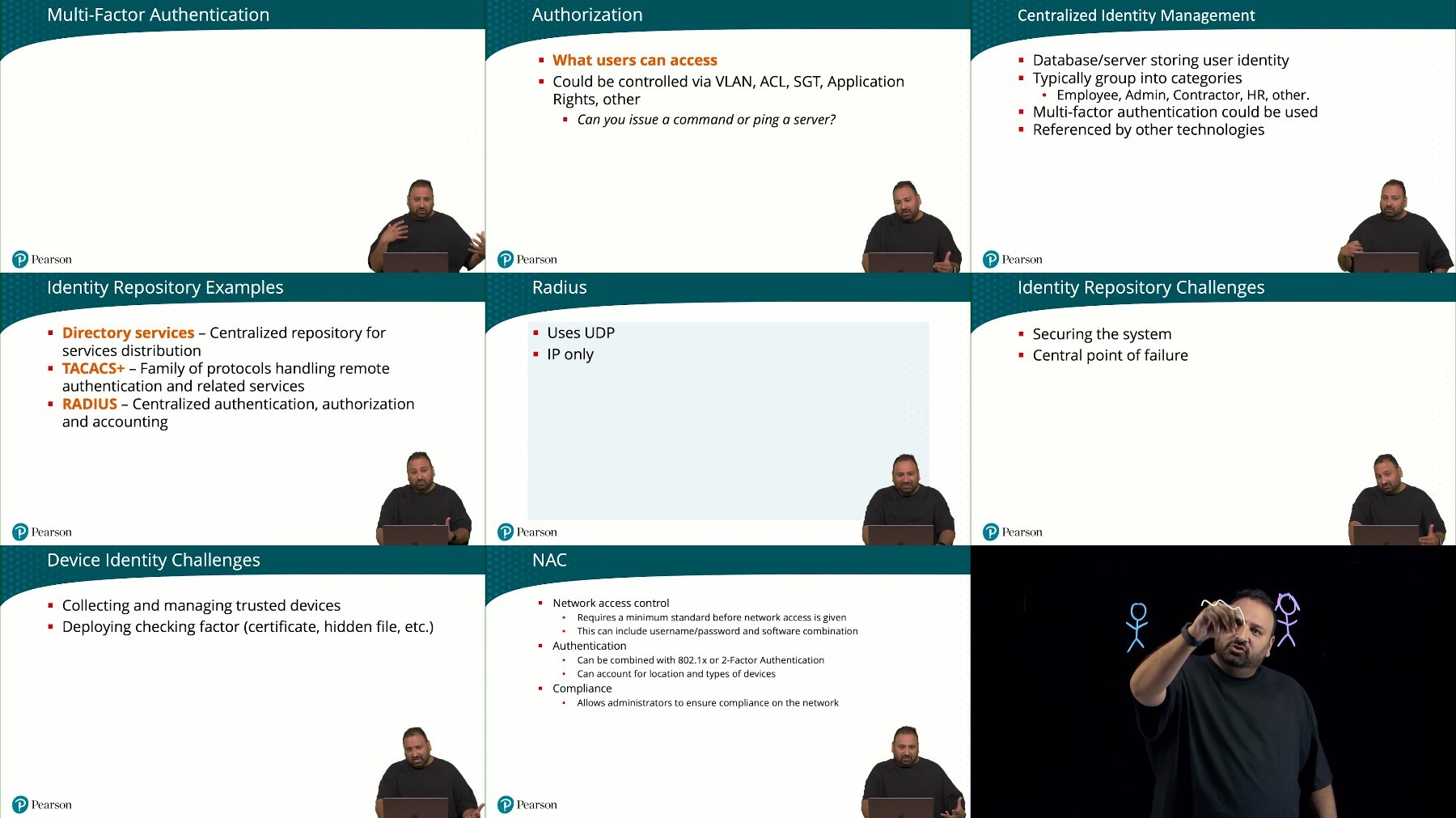
Screenshot
DDownload
https://ddownload.com/k8bm5avblxr5/Cybersecurity.Prevention.and.Detection.2nd.Edition.Video.Collection.part1.rar
https://ddownload.com/4a1pmkmuvz2n/Cybersecurity.Prevention.and.Detection.2nd.Edition.Video.Collection.part2.rar
RapidGator
https://rapidgator.net/file/17b10e3833aabdbd41b69e2187229267/Cybersecurity.Prevention.and.Detection.2nd.Edition.Video.Collection.part1.rar
https://rapidgator.net/file/bbe97b2ccfb8cb1e88945eccd9e7fe49/Cybersecurity.Prevention.and.Detection.2nd.Edition.Video.Collection.part2.rar
TurboBit
https://turbobit.net/knjflowrwlei/Cybersecurity.Prevention.and.Detection.2nd.Edition.Video.Collection.part1.rar.html
https://turbobit.net/2l9z3mbfwc76/Cybersecurity.Prevention.and.Detection.2nd.Edition.Video.Collection.part2.rar.html
Join to our telegram Group
Information
Users of Guests are not allowed to comment this publication.
Users of Guests are not allowed to comment this publication.
Choose Site Language
Recommended news
Commented



![eM Client Pro 9.2.1735 Multilingual [Updated]](https://pikky.net/medium/wXgc.png)





![[PORTABLE] PilotEdit 16.7 Multilingual](https://i.postimg.cc/598tqf3T/Pilot-Edit.png)
![Movavi Video Editor 24.0.2.0 Multilingual [ Updated]](https://pikky.net/medium/qhrc.png)

