Most Commented
Palo Alto FirewAll Pcnsa V11 Training





Description material

Palo Alto Firewall Pcnsa V11 Training
Published 10/2024
MP4 | Video: h264, 1920x1080 | Audio: AAC, 44.1 KHz
Language: English | Size: 14.14 GB | Duration: 19h 40m
Learn Palo Alto Firewall PCNSA PAN-OS Version 11 with Step-by-Step Lab Workbook
What you'll learn
Introduction and Initial Configuration
Palo Alto Firewall Installation
Configure and work with Palo Alto Firewall
Palo Alto Firewall NAT configuration
Configuring security policies
Configuring security policies
Palo Alto Architecture
Managing Firewall Configurations
Interface Configuration
Managing Firewall Administrator Accounts
Security Zones
Different Zone Types
App-ID (Application Identity)
Security Profiles
URL Filtering
Encryption and Decryption
Monitoring and Reporting
Backup and Restore
Introduction to Panorama
Dynamic Updates
Requirements
Firewall Essentials: Configuration and Management (EDU-210) course
Palo Alto Firewall Version 11 Essentials Training
Description
PCNSA Version 11:Successful completion of this course should enhance the student's understanding of how to configure and manage Palo Alto Networks next-generation firewalls. The student should learn and get hands-on experience installing, configuring, managing, maintaining and monitoring Palo Alto Networks next-generation firewalls to protect the networks.PCNSA Course Description:This training is the most important course as it covers all the fundamentals to understand the Next-Generation Firewall from the ground up. Even experienced firewall engineers take a lot out of this course as it includes, besides the architecture and management essentials, topics like Application Identification, Content ID (IPS, Anti-Virus/-Spyware, URL Filtering, File Blocking), SSL Decryption and User Identification which are all features usually not supported by legacy firewalls.Outline:01. Introduction and Initial Configuration02. Palo Alto Architecture03. Configuring Initial Firewall Settings04. Managing Firewall Configurations05. Interface Configuration06. Managing Firewall Administrator Accounts07. Connecting Firewall to Production Networks08. Security Zones09. Different Zone Types10. Creating and Managing Security Policy Rules11. Creating and Managing NAT Policy Rules12. App-ID (Application Identity)13. Security Profiles14. Objects15. URL Filtering16. WildFire17. User-ID (User Identity)18. Encryption and Decryption19. Monitoring and Reporting20. Backup and Restore21. Introduction to Panorama22. Dynamic UpdatesProduct Versions:Palo Alto Firewall Version 11.0.0Objectives:After completing this course, you should be able to:o Install and configure new Palo Alto Networks Next-Generation Firewalls.o Manage the Palo Alto Next-generation Firewall's configurations.o Configure the Firewall to connect to your production network.o Manage the Security Policy Rules used to protect your network.o Maintain and enhance the configuration of a virtual or logical router.o Create and apply security zones to policies.o Maintain firewall configurations.o Manage Network Address Translation (NAT) Rules.o Configure and manage Palo Alto Networks next-generation firewalls.o Configuring, managing, and monitoring a firewall in a lab environment.o Configure & manage essential features of Palo Alto next-generation firewalls.o Configure and manage Security and NAT policies to enable approved.o Configure and manage Threat Prevention strategies to block traffic.o Configure Policy based on application (App-ID) and user identity (User-ID).o Configure SSL Decryption on Firewall to inspect & control decrypted sessions.o Monitor network traffic using the interactive web interface and firewall reports.Prerequisites:Students must be familiar with networking concepts, including routing, switching, and IP addressing. Students also should be familiar with basic security concepts. Experience with other security technologies (IPS, proxy, and content filtering) is a plus. Recommended training includes the Firewall Essentials: Configuration and Management (EDU-210) course.Exam Blueprint:Management and Services 22%Managing Objects 20%Policy Evaluation and Management 28%Securing Traffic 30%
Overview
Section 1: Introduction
Lecture 1 PCNSA course Overview
Lecture 2 Basic Terminology
Lecture 3 CIA Triad Concepts
Lecture 4 Core Security Concepts
Section 2: Firewall Technologies
Lecture 5 Firewall Technologies Fundamentals
Lecture 6 Next Generation Firewalls
Lecture 7 Introduction to WAF
Lecture 8 Overview of Palo Alto Networks
Lecture 9 Zero Trust Security Principles
Lecture 10 Architecture of PA Firewalls
Section 3: EVE-NG LAB Setup
Lecture 11 Installing EVE-NG Version 6
Lecture 12 Adding SW images in EVE-NG
Lecture 13 Adding Other Images in EVE-NG
Lecture 14 Adding PA Firewall in EVE-NG
Lecture 15 Adding Panorama in EVE-NG
Lecture 16 Setting Up PCNSA Lab
Lecture 17 Importing Labs into EVE-NG
Section 4: Device & Network Configuration
Lecture 18 Configuring Devices
Lecture 19 Configuring DMZ Switch
Lecture 20 Configuring NTP Server
Lecture 21 Initial Configuration of PA
Lecture 22 Initial Configuration of HQ-FW
Lecture 23 Methods of Access PA Firewall
Lecture 24 Access PA Firewall Through API
Section 5: Palo Alto Networks Firewall
Lecture 25 PA Dashboard Walk-Through
Lecture 26 PA CLI Modes and Commands
Lecture 27 Configuring DNS & NTP in PA
Lecture 28 Concepts of Security Zones
Lecture 29 Practical Lab of Security Zones
Lecture 30 Concepts of Virtual Routers
Lecture 31 Practical Lab on Virtual Routers
Lecture 32 Interfaces of Palo Alto Firewall
Lecture 33 Layer 3 Network Interfaces
Lecture 34 PA Interface MGMT
Lecture 35 Practical Lab of VR Default Router
Lecture 36 Route Monitoring Overview
Lecture 37 Practical Lab of Path Monitoring
Section 6: Security Policies and NAT
Lecture 38 Concepts of Security Policies
Lecture 39 Practical Lab of Security Policies
Lecture 40 Understanding NAT
Lecture 41 Overview of Source NAT
Lecture 42 Overview of Destination NAT
Lecture 43 Practical Lab of Source NAT
Lecture 44 Practical Lab of Destination NAT
Section 7: SSL Decryption & Certificates
Lecture 45 SSL Decryption Overview
Lecture 46 Using Self-Signed Certificates
Lecture 47 Installing Certificate
Lecture 48 Practical Lab of Decryption Policies
Lecture 49 Verifying Decryption Policy
Section 8: Security Profiles
Lecture 50 Security Profiles Overview
Lecture 51 Security Profiles Deep Dive
Lecture 52 Practical Lab of Antivirus Profile
Lecture 53 Practical Lab of Anti-Spyware Profile
Lecture 54 Practical Lab of Vulnerability Profile
Lecture 55 Practical Lab of File Blocking Profile
Lecture 56 Practical Lab of WildFire Profile
Lecture 57 Practical Lab of Data Filtering Profile
Lecture 58 Security Group Overview
Lecture 59 Practical Lab on Security Groups
Section 9: URL Filtering Profile
Lecture 60 Overview of URL Filtering
Lecture 61 Malicious URLs Through Security Policy
Lecture 62 Malicious URLs Through URL Filtering
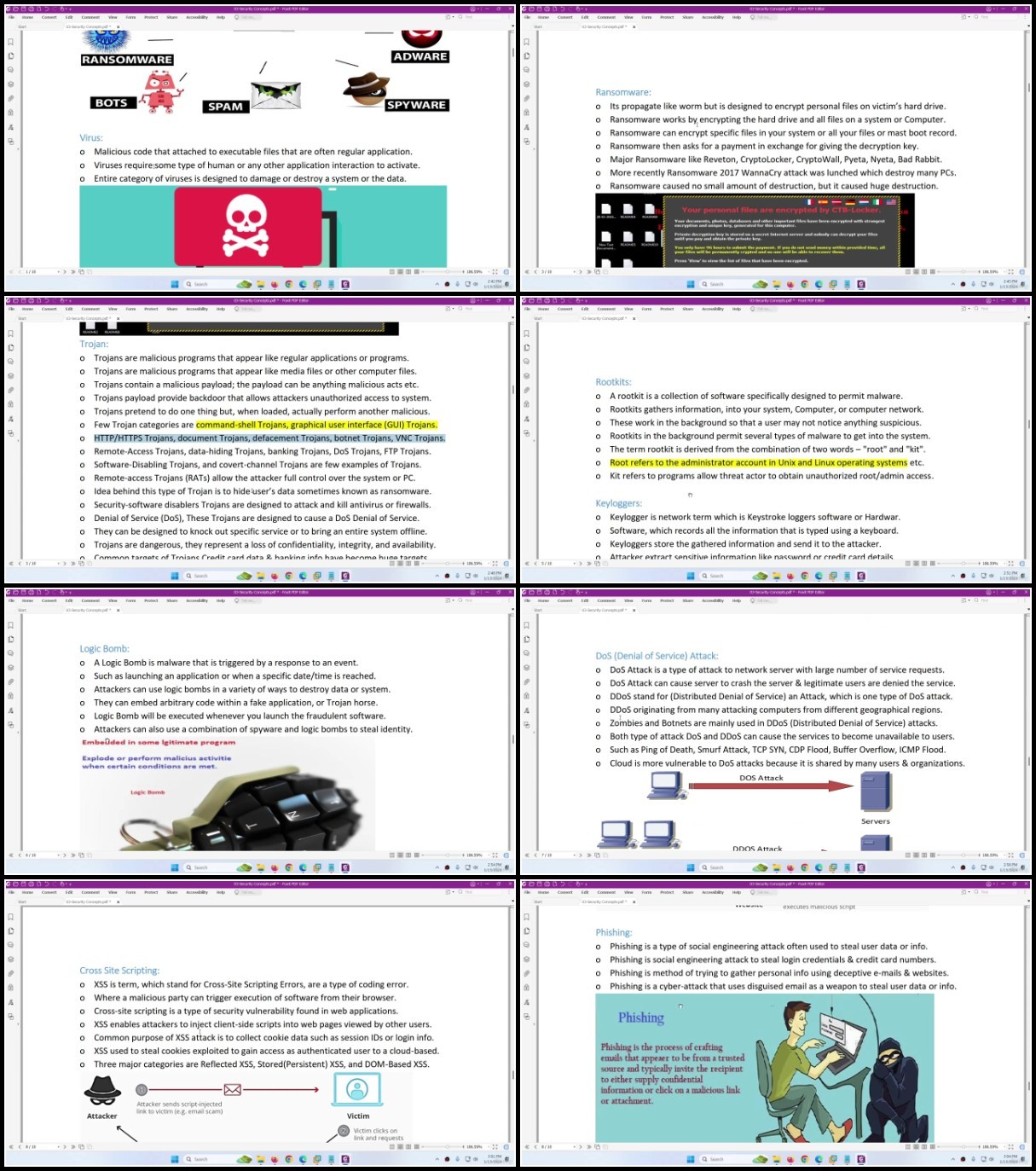
Lecture 63 Custom URL Category-Security Policy
Lecture 64 EDL to Block URL-Security Policy
Lecture 65 EDL & Custom URL-URL Filtering Profile
Section 10: DNS Security
Lecture 66 Overview of DNS Security
Lecture 67 Practical Lab of DNS Security
Section 11: APP-ID (Application Identification)
Lecture 68 Understanding App-ID
Lecture 69 App-ID Identification Methods
Lecture 70 App-ID Operation
Lecture 71 Application Shifts
Lecture 72 Application Window
Lecture 73 Dependent Applications
Lecture 74 Implicitly Use Application
Lecture 75 Application Groups
Lecture 76 Application Filters
Lecture 77 Application Block Page
Lecture 78 Identify Apps in SSL Traffic
Lecture 79 Policy Optimizer
Lecture 80 Application-ID Lab
Lecture 81 Port-Base to App-Base
Section 12: Tags and Groups
Lecture 82 Overview of Tags in PA
Lecture 83 Practical Lab of Tags
Lecture 84 Overview of Shadow Rule
Lecture 85 Static and Dynamic Group
Section 13: Service Route
Lecture 86 Overview of Service Route
Lecture 87 Service Route Configuration
Section 14: User-ID (User Identification)
Lecture 88 Overview of User-ID
Lecture 89 User Mapping Methods
Lecture 90 User-ID Agent Forms
Lecture 91 User-ID Operation DC
Lecture 92 Overview of Captive Portal
Lecture 93 Lab of Captive Portal
Lecture 94 AD Server Configuration
Lecture 95 Configuring Windows AD
Lecture 96 Configuring DNS Server
Lecture 97 User and Groups in AD
Lecture 98 PC1 Windows 11 Join AD
Lecture 99 Overview of User-ID Lab Setup
Lecture 100 Setting Up Service Account in AD
Lecture 101 Enable User-ID on The Inside Zone
Lecture 102 Configure LDAP Server Profile
Lecture 103 Configure User-ID Group Mapping
Lecture 104 Configure Integrated FW Agent
Lecture 105 Create User-ID Security Policy
Lecture 106 Test Security Policy with User-ID
Lecture 107 Verify The User-ID Configuration
Section 15: Administrator Accounts
Lecture 108 Overview of Administrator Accounts
Lecture 109 Administrator Roles
Lecture 110 Admin Authentication Methods
Lecture 111 Custom Admin Roles Lab
Lecture 112 Admin LDAP Authentication Lab
Lecture 113 Admin RADIUS Authentication Lab
Lecture 114 Admin Password Profiles
Lecture 115 Authentication Sequence
Section 16: Logs and Reports
Lecture 116 Palo Alto Firewall Logs
Lecture 117 Practical Lab of Logs
Lecture 118 Reports in PA Firewall Part-1
Lecture 119 Reports in PA Firewall Part-2
Lecture 120 Overview of Session Browser
Lecture 121 Overview of App Scope
Lecture 122 Dashboard for Recent Information
Lecture 123 ACC (Application Command Center) Tab
Security Analysts,Support Staff,Security Engineers,Security Administrators,Security Operations Specialists,Pre-sale System Engineers,System Admin,System Integrators,Resellers
https://fikper.com/75Wov0WQ3X/Palo.Alto.Firewall.PCNSA.V11.Training.part1.rar.html
https://fikper.com/06Vde5336w/Palo.Alto.Firewall.PCNSA.V11.Training.part2.rar.html
https://fikper.com/Q5fMh6UhNa/Palo.Alto.Firewall.PCNSA.V11.Training.part3.rar.html
https://fikper.com/PugLUuD5mQ/Palo.Alto.Firewall.PCNSA.V11.Training.part4.rar.html
https://fikper.com/zDiGe6J5Oq/Palo.Alto.Firewall.PCNSA.V11.Training.part5.rar.html
https://fikper.com/cgCTEl5nVW/Palo.Alto.Firewall.PCNSA.V11.Training.part6.rar.html
https://fikper.com/GUb3zCTLvi/Palo.Alto.Firewall.PCNSA.V11.Training.part7.rar.html
https://fileaxa.com/2j41somvc7a0/Palo.Alto.Firewall.PCNSA.V11.Training.part1.rar
https://fileaxa.com/yigdyn9y4t35/Palo.Alto.Firewall.PCNSA.V11.Training.part2.rar
https://fileaxa.com/ycwyfew7jesv/Palo.Alto.Firewall.PCNSA.V11.Training.part3.rar
https://fileaxa.com/d0iwxdp9wg7a/Palo.Alto.Firewall.PCNSA.V11.Training.part4.rar
https://fileaxa.com/x8mtw755shb7/Palo.Alto.Firewall.PCNSA.V11.Training.part5.rar
https://fileaxa.com/z0lenxopkc23/Palo.Alto.Firewall.PCNSA.V11.Training.part6.rar
https://fileaxa.com/637be4uzekif/Palo.Alto.Firewall.PCNSA.V11.Training.part7.rar
https://rapidgator.net/file/52401bf0462b5fdd2f283299082ff35e/Palo.Alto.Firewall.PCNSA.V11.Training.part1.rar
https://rapidgator.net/file/cf20838ceea17f30f822f763b97d5b4d/Palo.Alto.Firewall.PCNSA.V11.Training.part2.rar
https://rapidgator.net/file/184f54af0d2a9defd58c84696352f50d/Palo.Alto.Firewall.PCNSA.V11.Training.part3.rar
https://rapidgator.net/file/bae8577b47187cd09c81cc596fa56fe5/Palo.Alto.Firewall.PCNSA.V11.Training.part4.rar
https://rapidgator.net/file/fcc4d334419ea018720663866dda5cab/Palo.Alto.Firewall.PCNSA.V11.Training.part5.rar
https://rapidgator.net/file/bd1ccfc8ee81e6ded16691d24232d89e/Palo.Alto.Firewall.PCNSA.V11.Training.part6.rar
https://rapidgator.net/file/c48e531dbd7b6370ecd290716df74861/Palo.Alto.Firewall.PCNSA.V11.Training.part7.rar
https://turbobit.net/yiunynm8q404/Palo.Alto.Firewall.PCNSA.V11.Training.part1.rar.html
https://turbobit.net/v0zutg7qvyiu/Palo.Alto.Firewall.PCNSA.V11.Training.part2.rar.html
https://turbobit.net/xbvokrxfjsnw/Palo.Alto.Firewall.PCNSA.V11.Training.part3.rar.html
https://turbobit.net/5cbo59h8v9fo/Palo.Alto.Firewall.PCNSA.V11.Training.part4.rar.html
https://turbobit.net/gsb1c4n1x5pi/Palo.Alto.Firewall.PCNSA.V11.Training.part5.rar.html
https://turbobit.net/xo2zqjtf305u/Palo.Alto.Firewall.PCNSA.V11.Training.part6.rar.html
https://turbobit.net/rc6d4i52i90e/Palo.Alto.Firewall.PCNSA.V11.Training.part7.rar.html

Join to our telegram Group
Information
Users of Guests are not allowed to comment this publication.
Users of Guests are not allowed to comment this publication.
Choose Site Language
Recommended news
Commented


![eM Client Pro 9.2.1735 Multilingual [Updated]](https://pikky.net/medium/wXgc.png)






![Movavi Video Editor 24.0.2.0 Multilingual [ Updated]](https://pikky.net/medium/qhrc.png)

